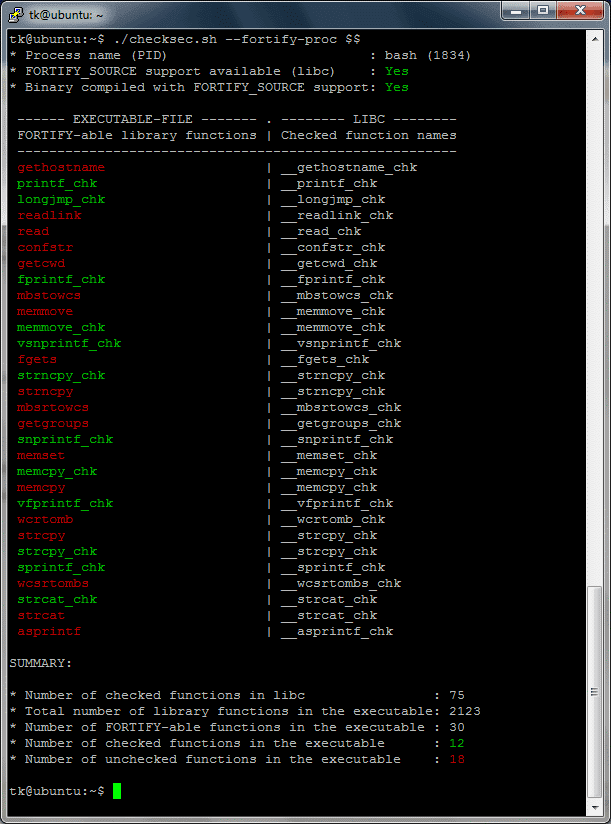
checksec.sh
Version 1.4 now supports FORTIFY_SOURCE.
January 14, 2011
What's New?
- Support for FORTIFY_SOURCE (--fortify-file, --fortify-proc).
- Check if the readelf command is available.
- readelf support for 64-bit ELF files.
- Check if the requested files and directories do exist.
- --dir is now case-sensitive and correctly deals with trailing slashes.
- Check user permissions.
fortify-file Usage Example.
The following test program is vulnerable to a stack buffer overflow (see line 10):
#include <string.h>
#include <stdio.h>
int
main (int argc, char* argv[])
{
int a = 1;
char buf[12];
strcpy (buf, argv[1]);
printf ("%08x\n", a);
return 0;
}Compile the test program without stack canary support (-fno-stack-protector) and without FORTIFY_SOURCE:
$ cat /etc/lsb-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=10.10
DISTRIB_CODENAME=maverick
DISTRIB_DESCRIPTION="Ubuntu 10.10"$ gcc -fno-stack-protector -o testcase testcase.cCheck the compiled executable with checksec.sh:
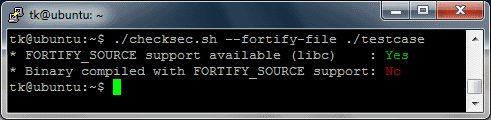
The output of the script shows that, as expected, FORTIFY_SOURCE is not supported by the executable. Next, we overflow the stack buffer by providing an overly long command line argument to the test program:
$ ./testcase AAAABBBBCCCCDDDD
44444444As can be seen from the output above, the stack variable a was successfully overwritten with our overly long command line argument (a was overwritten with the supplied D's or 0x44 in hexadecimal). Next, we compile the test program with FORTIFY_SOURCE support but without stack canaries and check the executable file with checksec.sh again.
ⓘ Note
Under Ubuntu FORTIFY_SOURCE is used when compiled with -O2 or higher. On other Linux distributions (e.g. Fedora or openSUSE) you need to add the compiler flag -D_FORTIFY_SOURCE=2.
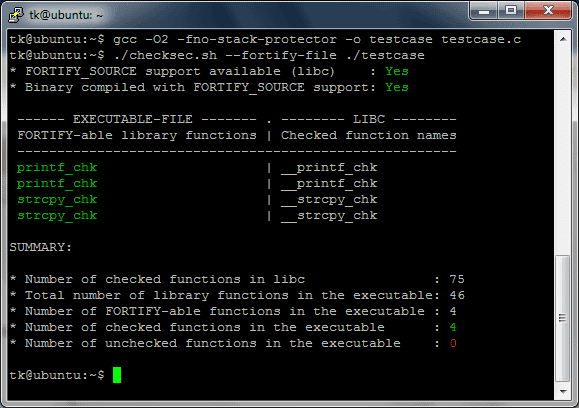
The above output of checksec.sh shows, that the executable was successfully compiled with FORTIFY_SOURCE. Now lets try to overflow the buffer again.